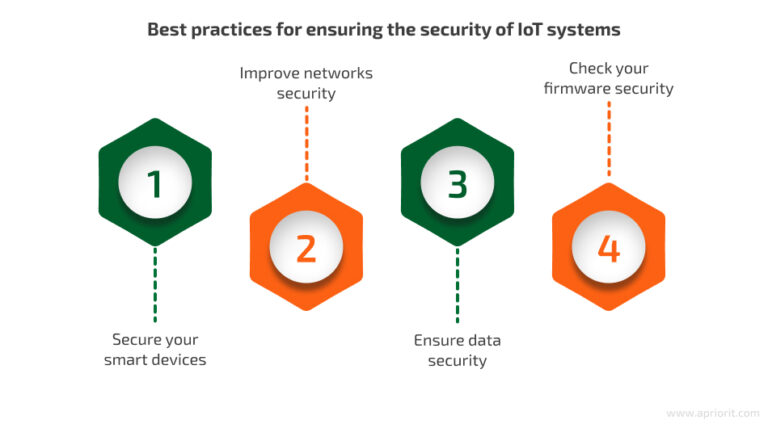
IoT Protocols MQTT and CoAP are riddled with vulnerabilities The Circuit Diagram 8 Best practices to improve your IoT security . Securing the IoT infrastructure is critical, but it requires a robust strategy to effectively secure data in the cloud and protect data integrity in transit. Here are some of the best practices to improve IoT security for your organization. 1. Track and manage your devices IoT security best practices. To ensure IoT device security and IoT network security, here are some best practices to bear in mind: Keep up to date with device and software updates. When buying an IoT device, check that the vendor provides updates and consistently apply them as soon as they become available. Software updates are an essential

Educate users about the importance of IoT security and best practices for safeguarding devices. Training should include recognizing phishing attempts, securing home networks, and reporting suspicious activity. 7. Develop a Comprehensive Security Policy. Create a security policy that outlines the procedures and protocols for securing IoT devices.
Top 10 Internet of Things (IoT) Security Best Practices Circuit Diagram
creating future security standards. It prioritizes practices which might be most relevant to IoT and which might encourage standards and policies to improve IoT security. This is certainly not an exhaustive list of best practices. It is simply an attempt to help avoid some of the most serious and well known flaws in IoT practice today. The following diagram shows a high-level view of the components in a typical cloud-based IoT solution. This article focuses on the security of a cloud-based IoT solution: You can divide security in a cloud-based IoT solution into the following three areas: Device security: Secure the IoT device while it's deployed in the wild.

The IoTSF Best Practice Guidelines cover various aspects of IoT security, including secure development, secure deployment, data privacy, and the management of security incidents. Each section provides clear and concise recommendations, which can be easily followed by IoT professionals and organizations.

Understanding IoT Security: Threats, Standards & Best Practices Circuit Diagram
To help prioritize IoT Zero Trust investments, you can use the Industry IoT Consortium's (IIC) IoT Security Maturity Model to help assess the security risks for your business. Zero Trust principles and best practices for end-to-end security. When designing an IoT solution, it is extremely important to identify and understand potential threats
